A joint group of specialists from the National Center for Scientific Research of France and the Graz Technical University published a report on new attack vectors for AMD processors. Researchers said AMD processors are vulnerable to two attacks.
These problems, discovered by experts back in 2019, affect the security of data processed by processors and can lead to theft of confidential information, as well as security impairment.
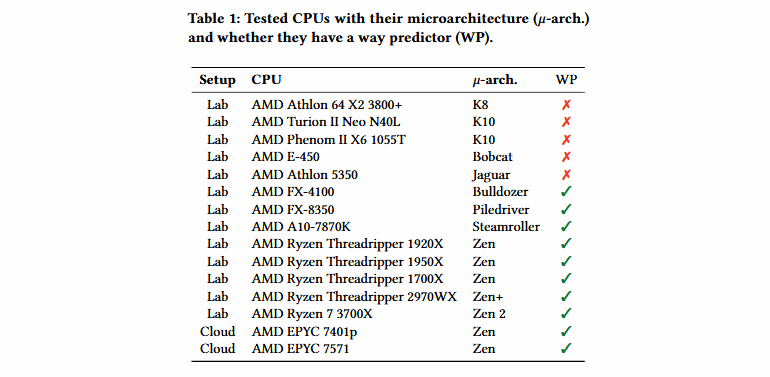
It is reported that AMD processors, released between 2011 and 2019, are vulnerable to bugs (the table can be seen below). Moreover, the researchers notified AMD engineers about their findings back in August 2019, but the company did not consider it necessary to issue patches, since it did not consider these problems to be the new speculative (or proactive – speculative) attacks. Of course, researchers disagree with this.
Problems discovered by experts affect predictor mechanism in the L1D Layer 1 data cache. This performance-oriented functionality was introduced in AMD processors in 2011, it reduces power consumption.
So, according to a published report, the way predictor calculates µTag by applying an undocumented hash function to the virtual address. ΜTag is then used to determine the cache channel from the table. That is, the processor should not compare the cache tag with all possible options, which can reduce energy consumption.
“Our attacks demonstrate that AMD architecture is vulnerable to attacks on third-party channels,” scientists say.
Researchers managed to reverse the mentioned “undocumented function” used by AMD processors and detect two attack vectors: Collide + Probe and Load + Reload. These side-channel attacks are in many ways similar to the classic Flush + Reload and Prime + Probe, which were previously used by other information security experts to extract data from Intel processors.
At the same time, the authors of the report are sure that the problems they discovered differ from other attacks through third-party channels. Therefore, in their opinion, Collide + Probe and Load + Reload are not theoretical attacks, but problems that can be easily used in real life, and for it, the attacker does not need physical access or special equipment. For example, experts claim that they exploited attacks in the cloud using JavaScript.
So, during one experiment on the AMD processor, it was possible to launch a malicious process that used a hidden data extraction channel to steal data from another process. The rate of “discharge” of data was 588.9 Kb/s.
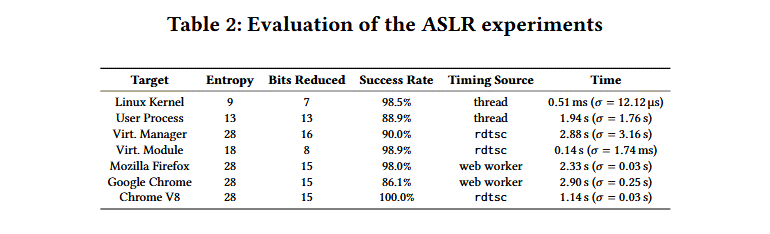
The Collide + Probe attack was adapted to reduce the entropy of various ASLR (Address Space Layout Randomization) implementations. If the attacker managed to circumvent ASLR protection, he actually gets the opportunity to predict where the code will be executed, and plan further attacks.
Researchers said they compromised the ASLR core in a fully updated Linux system, as well as ASLR for operating systems and applications running in cloud and virtual environments. These attacks required the introduction of malicious code on the target machine, however, it is reported that the attack is possible through the Internet: using malicious JavaScript in the browser.
“We tested our proof-of-concept on Chrome 76.0.3809 and Firefox 68.0.2, as well as on the Chrome V8 engine. In Firefox, we were able to reduce entropy by 15 bits with a 98% success rate and average run time of 2.33 s (σ = 0.03s, n = 1000). In Chrome, we achieved a success rate of 86.1% and an average lead time of 2.90s (σ = 0.25s, n = 1000)”, — experts write.
In addition, the Collide + Probe attack was successfully used to recover an encryption key from an AES T-table implementation.
On Twitter, one of the experts publicly admitted that the found bugs could not be compared with Meltdown and Zombieload, which Intel processors are subject to.
“Is this vulnerability as severe as Meltdown or Zombieload? Certainly not. The attacks leak a few bit of meta-data. Meltdown and Zombieload leak tons of actual data”, – said Daniel Gruss (@lavados).
The official AMD announcement says that the company does not consider the described problems as new speculative attacks, since these problems are solved by installing other previously released fixes for old side-channel problems.
Let me remind you that in past years AMD processors were recognized as vulnerable to such side-channel problems as Specter v1 (CVE-2017-5753), Specter v1.1 (CVE-2018-3693), Specter v1.2, Specter v2 (CVE -2017-5715), CVE-2018-3640, SpectreNG (CVE-2018-3639), SpectreRSB, NetSpectre, as well as a set of bugs L1TF (L1 Terminal Fault) or Foreshadow.
In turn, the researchers assured reporters of the ZDNet publication that AMD’s response was “very misleading,” and the company did not interacted with a team of experts since last August, that is, since the private disclosure of information about the problems. In addition, the attacks themselves supposedly to this day work on completely updated OS, with the latest firmware and software.
However, vendors are not the first to postpone solutions to problems and thereby endanger users.