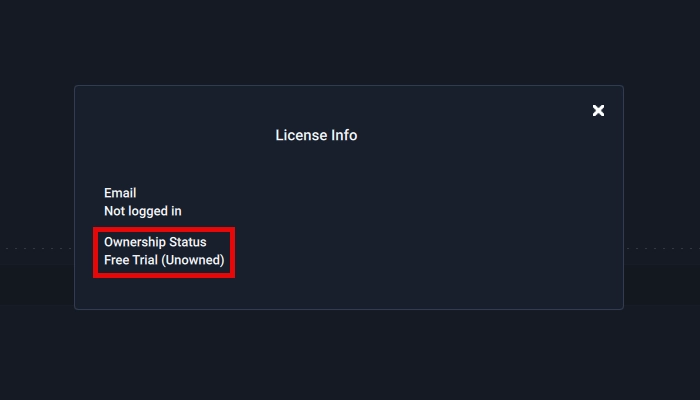
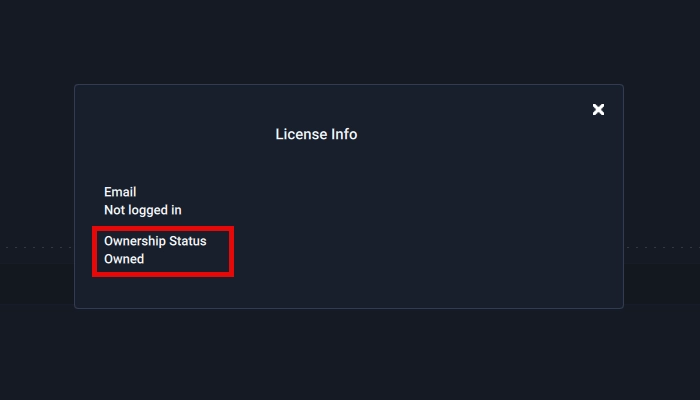
HackTool:Win32/Crack is related to hacking tools for bypassing license verification. These are often activators of Windows, MS Office, and other proprietary software. Contrary to the widespread belief that such tools are safe, they can carry a threat.
The most popular sources of such hacking tools are torrent distributions and websites with hacked software. Let me explain, what hacked software is, what risks its use entails, and whether it is profitable to use it compared to licensed software.
What is HackTool:Win32/Crack
HackTool:Win32/Crack is a generic detection that Microsoft Defender attributes to a piece of code that bypasses the license check. It is worth clarifying that it rarely refers to a stand-alone program but to a modified element of a benign app. Win32/Crack means a change in the program files or a part of it aimed at disabling the license verification mechanism.
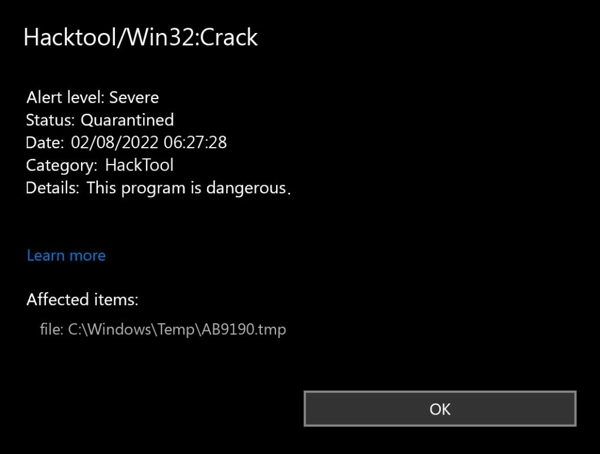
Win32/Crack is often distributed via torrents or websites dedicated to cracked software that has its licensing system tweaked or disabled. It can be either a separate file or embedded into the executable file of the target program. By its nature, HackTool:Win32/Crack does not pose a direct threat to the system, even though the thing it does is illegal. The Defender’s detection of such tools is compulsory to fight piracy.
Is Hacktool:Win32/Crack Dangerous?
Although Win32/Crack is not dangerous, a lot of them come with other malware embedded in the same executable file. Particularly greedy authors of such software do this to monetize their effort. Such “bonuses” can include infostealers and more severe malware like ransomware. As a result, instead of saving money, the user pays a higher price, in the form of stolen confidential data or encrypted files.
How does Win32/Crack Work?
There are two different types of software cracking: by making the program believe it has a proper activation and by disabling this check completely. Both have pros and cons, and both are illegal to perform and use. Let’s have a closer look at how this works.
The methods of software cracking below are listed exclusively for educational purposes. I discourage using unlicensed software, due to both legal dangers and malware hazards. These hacking approaches are here to make a clear understanding of what exactly Microsoft Defender means as Win32/Crack.
Disabling the license check
One way to protect software from unauthorized use is by including a check license function in its startup procedures. Essentially, the software program is a set of instructions, represented as a series of bytes, executed by the CPU. During reverse engineering, the checkLicense section is identified and decompiled. A programmer may patch the binary by replacing specific bytes to bypass the check license requirement.
The patched bytes typically satisfy the check license requirement by writing values into registers or memory addresses or returning a particular status code. After patching the binary, the handyman manipulates the check license function, and the software program is considered “cracked.” However, with most apps now checking keys on their servers, this method is becoming less common.
Embedding the key
Such a crack approach emulates an online key verification process and results positively without a real internet connection. Often, in the instructions for using the app, one of the points is “deny the application access to the Internet”. This is because the license will be deactivated once the app connects to the server and uncovers that it is fake. These days, most cracks are not dependent on the connection and allow you to enter any text instead of the key.
In the real world, things are more complicated now, as the software will “phone home” and see if those keys are any good. This can be bypassed by sniffing/decrypting HTTPS traffic and finding the Web request that asks if the key is valid. From there, it can be intercepted, thus never letting the request reach its final destination and replying with your own (fake) response.
Handyman can make this or log and copy an already valid response. The program will believe it got the go-ahead from the server and continue operating as normal. In that case, you can/need to modify the binary so that it always thinks the answer from the server is positive. Another trick of this grade is to run a fake HTTP server that always replies positively and redirects the check.
Is it a False Positive?
In most cases, HackTool:Win32/Crack is not a false positive, with just a few exceptions. As I said at the beginning, it detects specific changes done to the program file. Microsoft Defender can mistakenly detect HackTool:Win32/Crack if there are changes in the program’s code that could be interpreted as signs of a crack. For instance, if a program uses code strings, jumpers or calls typical for Win32/Crack, the antivirus might incorrectly classify it as one. In such cases, I recommend you check the file using our free online checker.
Safety Recommendations
I’d emphasize once again – do not use pirated software at all for your safety. In addition to being illegal, pirated software is a breeding ground for malware. Once a user adds any malware or potentially unwanted software to the antivirus exceptions, it can take on a life of its own. Therefore, if you see HackTool:Win32/Crack detection, download GridinSoft Anti-Malware and perform a full scan of your device.