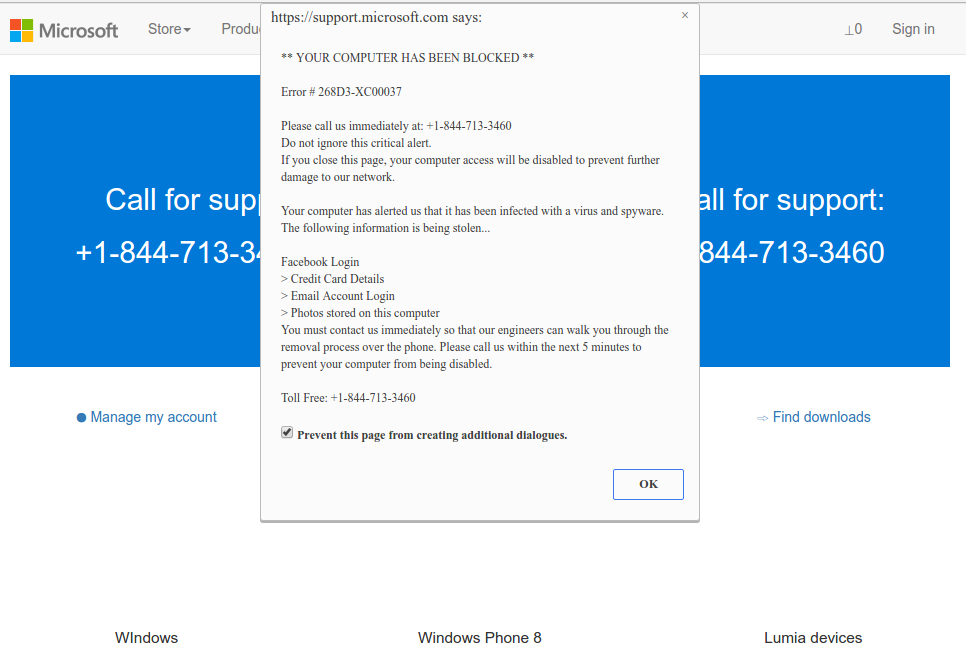
The new sector of cyber attacks has become popular nowadays. In the guise of Microsoft Technical Support (Microsoft Tech Support Scam). Scammers try to force Internet users into making a call on an alleged toll-free phone number. Of course, this number isn’t free indeed, and the fraudsters gain money from each call.
Due to many of our users claims about such cyber attacks, we’ve decided to make a detailed investigation into this fraudulent scheme. In this post, we will give you the answers to the most frequently asked questions about Microsoft Tech Support scammers. Forewarned is forearmed! We hope that you will be attentive to the signs and take care of your safety while browsing. Don’t let scammers to manipulate on your fears!
How scammers scare people?
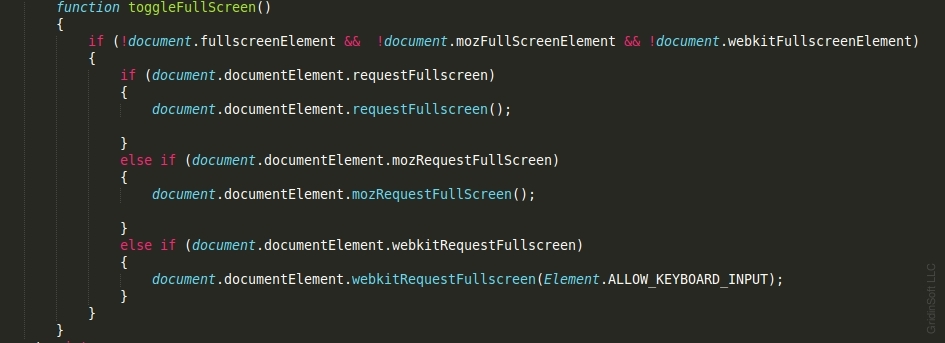
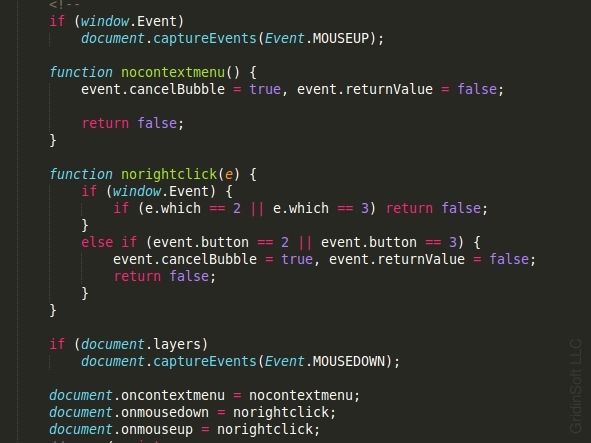
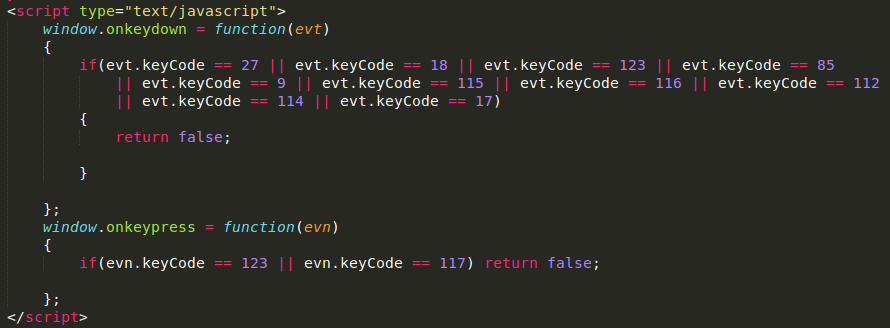
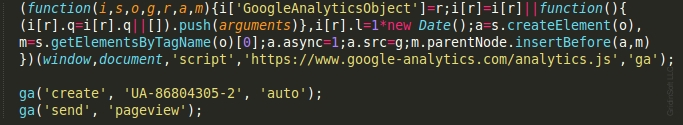
Hackers use similar methods to scare their victims, with their main goal being to gain profit. Fraudulent landings can toggle full-screen mode, lock the pressing of the main keys and stop the context menu launching. These scamming actions can be easily done by using the following javascript code:
Amusingly, but the fraudsters even connect the Google Analytics to their malicious web pages!
The horrible text messages are not the only thing which scammers are using to terrify their victims. There are also threatening voice notifications played. Usually, they are stored here:
* MALICIOUS_URL * / chrm / alert2.mp3
If you ever encounter one of these scare tactics, just keep calm and believe that there is no real danger, if you’re not calling the “free” phone number of the fake technical support team.
Scam-as-Service: how it works?
The landing pages, which our users were unhappy to see, are just the tip of the iceberg. Malware-as-Service has been thriving in the cybercrime world for a long time, and as for these new scam techniques, they should be called Scam-as-Service.
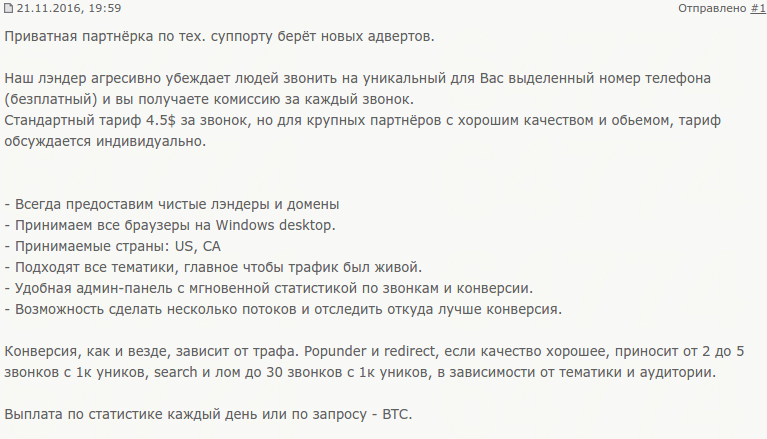
On a recently, discovered semi-private Russian underground forum exploit.in, we stumbled upon an affiliate program’s description:
English translation:
- Always provide clean landings and domains.
- Accept all browsers for the Windows desktop.
- Accepted countries: US, CA
- All subjects are suitable, the main thing was that the traffic was alive.
- Handy admin panel with the instant statistics of calls and conversion.
- The ability to make multiple streams and their conversion’s comparison.
Conversion, as elsewhere, depends on the traffic’s quality. If the quality is good, the popunder and the redirect bring from 2 to 5 calls from 1k unique visitors. The search and scrap bring up to 30 calls from the 1k unique visitors, depending on the subject and the audience. You’ll get your payments every day or O/R – BTC. The usual working time is from 19:00 to 02:00. But, it’s highly recommended to ask the support if it has changed each time before delivering the traffic.
As you can see from the description, the scheme is quite simple: the creators of the affiliate program provide publishers with domains, admin panels with statistics, and payments through the BTC (which became the standard currency in the cyber underworld). Publishers should only send the traffic to the affiliate domains and wait for the profit.
Could Google eliminate this fraud?
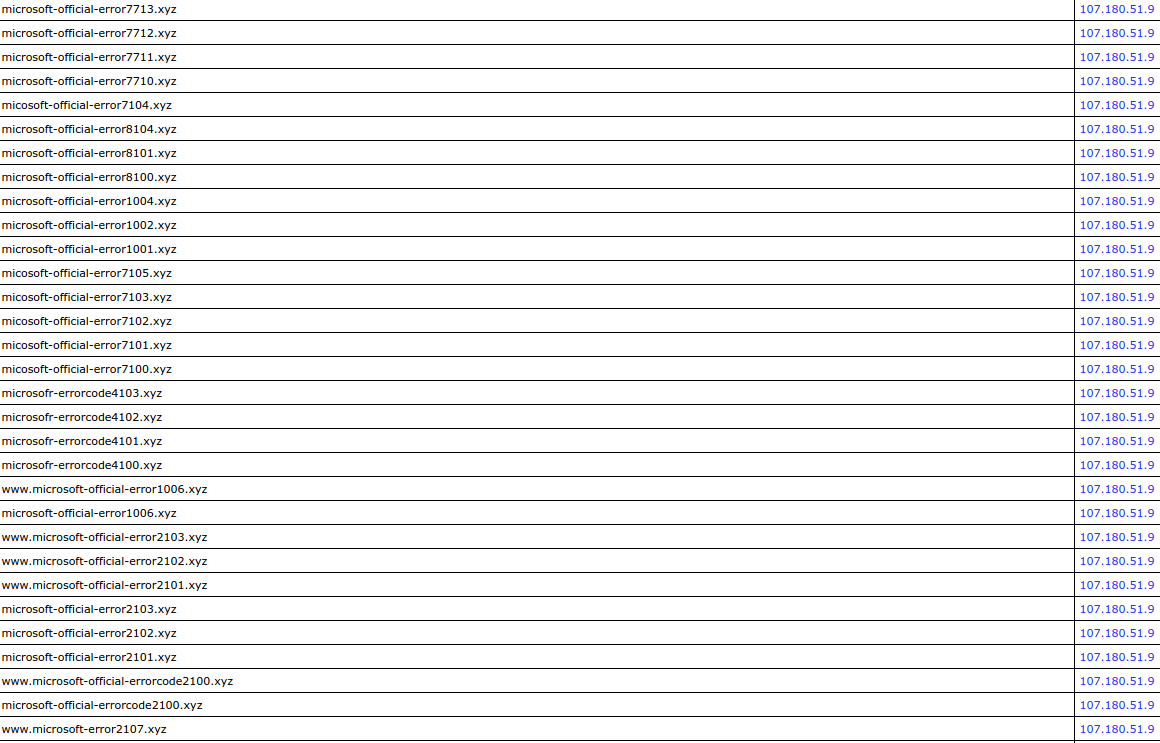
Google can quickly defuse such aggressive scams by adding fraudulent landings to the Google Safe Browsing filters. But, the scammers do not give up easily. They register a large amount of similar domains with similar names (trying to allude Microsoft):
So, bear in mind, that the lifetime of the separate scam pages is very short. They shouldn’t scare you at all.
What happened with those who made a call?
There is the same phone number for all scammers pages: +1-844-713-3460. We gathered the typical user complaints on this number:
As is clear from the users’ complaints, the scammers are trying to make the victim give them full access to the computer for further intimidation. You shouldn’t give access to your system to anyone unfamiliar with the web, especially if they insist on undertaking these suspicious actions themselves.
Conclusion:
Microsoft Tech Support scam – new widespread scheme in the cybercrime world. Scammers make money from the user’s fears by scaring people with the same simple techniques. Usually, keys are blocked, full-screen mode, and horrible audio messages. I hope we have convinced you that you shouldn’t be afraid and give hackers what they want. Such deceptive and primitive schemes don’t deserve your sponsorship!