What is Mimikatz?
April 12, 2023
Mimikatz is a hack tool that was created to dig into Windows system mechanisms and collect the passwords related to Microsoft services. It gathers such data from all users on the host PC, and also from all computers in the local area network. Mimikatz is a free open-source software that is available on GitHub. Benjamin Delpy, its developer, asked Microsoft to pay attention to these security flaws, but the company rejected his reports. After a couple of years, in 2012, understanding the might of these and his exploit tool, Benjamin released the source code. Cybercriminals appreciated the potential of this tool, and it became a lockpick for crooks that try to get access to the entire network after getting to a single computer.
Contrary to more classic brute force approaches, Mimikatz offers to get the passwords through breaking into Windows authentication mechanisms - both related to the system and to the network services. In particular, it may obtain not only local PC passwords, but also get so-called silver and golden tickets, that go from the network administrator’s name. It supports different types of system authentication, as it was changing through sequential Windows updates. In latest updates Mimikatz also received the ability to do the same trick with *NIX systems.
Mimikatz modules
Long evolution process brought 4 functional modules that are embedded into Mimikatz, along with 12 core elements. They generally pose as alternative modes of work, which contain the functions needed for hacking different system elements. Their names generally correspond to their purpose. In some cases, they’re combined with each other. Core modules, at the same time, provide basic functionality, like listing users, processes, escalating privileges, and so on.
| Function name | Description |
|---|---|
| Crypto | Provides a token impersonation ability through CryptoAPI exploitation. |
| Sekurlsa | Extracts pin codes, tickets, keys or passwords from the LSASS.exe process memory. |
| Kerberos | Exploits Kerberos API in order to extract so-called gold and silver tickets. |
| Lsadump | Operates with Security Account Managers (SAM) data, that generally handles the password hashes. |
Windows and Mimikatz
To have a better understanding of how this hacktool makes its way to users’ credentials, you should have a look at how Windows authentication works. Different versions of this OS managed it in different ways, and Mimikatz evolved along with these approaches. Despite being rendered less effective for short periods of time after the update, it received all things it needs for success with even the latest Windows versions.
At the moment of its initial release in 2007, Mimikatz was aiming at flaws of data handling security in Windows 2000 Server/Windows Server 2003. Those were flaws in Active Directory – actually, the directory service for controlling the domain networks. It was keeping the passwords in a plain text form within the files related to the AD services. With a simple manipulation of these files, it was possible to obtain the contents – passwords and their hashes. This data pair is enough to use all the accounts present in the network controlled with AD.
Further, Microsoft abandoned these methods of password handling. But other solutions used by Microsoft were not perfect either. Kerberos TGT, which works jointly with the LSASS process, can be exploited to extract the ticket (a short-term “pass” that allows the user to authenticate). The problem here lies in the way Windows handles these tickets – they can easily be obtained through scanning the logon events or decrypting the memory of the aforementioned LSASS process.
Other approaches are no better than ones we mentioned earlier. This or another way, they have breaches that allow Mimikatz to extract the login credentials, if they’re stored locally. Hence, the only real way to give this and other hacktools no chance for success is to use login methods offered by Microsoft as Windows Hello. In that case, all the login data is stored on Microsoft servers, and the local system handles only a password.
Mimikatz spreading and usage
Before getting under the hood of this utility, let’s have a look at how it arrives on target systems. We’re leaving aside the cases when Mimikatz is installed intendedly, as it does not pose any threat in that case. Most commonly, this hacktool comes as a part of a malware bundle, together with the main payload. In the case of a corporate-scale cyberattack, such a bundle may contain a backdoor, network reconnaissance tool, ransomware or spyware as a main course, and Mimikatz. The latter, together with network recon, provides cybercriminals with all login credentials for Microsoft services. As you can guess, Mimikatz is pretty useless if network services within the company are organised with the use of a different set of utilities. Still, when used right, it may be even more effective than all "regular" password stealing tools.
Stand-alone usage of this hacktool is barely viable. To execute the commands remotely, it requires a backdoor access – so there should be auxiliary malware. Easy access to the source code in the Mimikatz GitHub repository made it a popular tool in tbe hands of amateur hackers. Generally, the efficiency of such attacks are pretty low, but there are exclusions like NotPetya ransomware attack. The latter included the use of a tweaked variant of Mimikatz to grab the passwords of the users within the attacked network.
List of hacker groups that are using (or used) Mimikatz
| Group name | Description |
|---|---|
| APT28 | Russian hacker group accused for intruding the US 2016 elections. Uses a fork of Mimikatz with their own modifications. |
| BadRabbit | An offspring of Petya/NotPetya (uses their codebase). Brings a separate instance of Mimikatz in its original edition. |
| APT21 | Chinese APT group, also known as HAMMER PANDA. Uses a manually modified version of Mimikatz. |
| Conti | Russian ransomware gang, defunct in May 2022. Was bringing original version of Mimikatz to dump network users' credentials. |
| Lazarus | Presumably North Korean APT group. Adjusted Mimikatz for their needs and brings its encrypted instance to each attack site. |
| Carbanak | Also known as FIN7. Used a regular Mimikatz along with the other open-source tool - PsExec. |
| FIN6 | Cybercrime gang involved in massive carding via attacking Point-of-Sale terminals. Used Mimikatz together with PsExec and AdFind. |
Mimikatz Explained: How Does it Work?
As we mentioned above, Mimikatz initially appeared in 2007 as a showcase of vulnerabilities in Windows authentication mechanisms. With the progression of auth methods used in the operation system, the developer added the ability to hack them as well. Overall, there are 5 possible ways of credentials stealing, including one that works on macOS, UNIX or Linux systems.
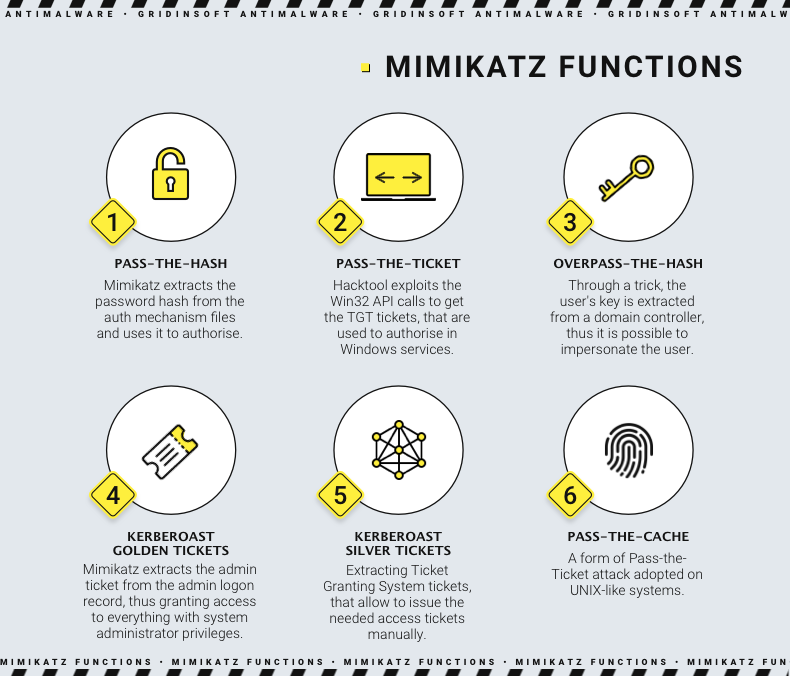
Pass-the-hash
The attack known as pass-the-hash is a historically first attack that Mimikatz was capable of. It was aiming at the mechanisms of Active Directory we described above. The key of attack was to dump the files that hold the data of users present in the system. Ntds.dit file contains password hashes which are used to simplify the further login attempts of the user that is already logged in.
In single-user systems, this attack way was running longer, and can still be possible time-to-time. Windows stores local user password hash in the memory of LSASS.exe process, in an encrypted form. When a login attempt happens, the system decrypts the hash and compares it to the hash of the input. Regardless of the result, it ciphers the data back. However, the encryption is managed with the use of regular LsaUnprotectMemory and LsaProtectMemory WinAPI calls. After getting to the memory allocated by the LSASS process, that is no problem with decrypting the parts that contain the hash.
Pass-the-ticket
In more modern Windows versions, Microsoft created a new login method based on Kerberos tickets, known as Ticket Granting Ticket, or TGT. Contrary to the system that was used before, this one offers a time-sensitive authentication, which already decreases the value of dumped credentials, as they're valid for 7 to 10 hours. This system supposes a completely different approach to authorisation handling, featuring the access granting only to a designated resource. Still, it has a couple of exploitable features, that can bring access to all services which are accessed with the use of Kerberos tickets.
Once again, Mimikatz plays with the LSASS.exe process in order to get the ticked data from its memory. It appears that the system stores tickets in a pretty much the same way as it does with passwords we described above. Through a simple manipulation, the hacktool extracts the ticket(s) with all the information needed for its correct usage. Then, another command from within the hacktool interface allows you to apply the ticket to your current profile, thus adopting the privileges of a person who owned the ticket initially. The only flaw that appears from collecting any tickets available is the fact they may have expired by the moment when Mimikatz has stolen them.
There is another utility issued by Benjamin Delpy, named Rubeus, that addresses this issue. It aims at commencing pass-the-ticket attack through a slightly different approach, still, only a couple of first steps differ.
Rubeus simply scans the logon for new entries that will correspond to the new logins into the system. These entries contain data of the users that are most likely active at the moment. Then, it simply dumps these tickets, and shows the output in its window. Same as in Mimikatz, a crook who manages this entire process may choose between the tickets, depending on their belonging to the interested resource. Using another program that can inject the outside tickets into the current session (Mimikatz is the one) it is possible to make the system think you’re the other user.
Kerberoast attack
Kerberoast, as you can suppose by its naming, supposes yet another exploiting of Kerberos authentication system. Same as pass-the-ticket, it touches the Ticket Granting Ticket mechanism, but this time involves ones that provide access to the services in the system at administrator level. It is done through both stealing the admin tickets, or spoofing the TGS tickets. Correspondingly, attacks are named as golden ticket and silver ticket attack.
Silver ticket attack supposes obtaining the tickets that belong to the account that manages ticket granting service (an aforementioned TGS). Decrypting the LSASS process memory, it is possible to extract TGS manager account’s ticket, and then use it to authenticate yourself as the one. Then, it is possible to issue almost any kind of ticket to the account you need. This variant of the Mimikatz usage is extremely dangerous if the TGS is managed by a single person, as spoofing its permissions will end up with the possibility of spoofing access rights of pretty much every user in the system.
What may be even worse for the target is a golden ticket attack. It aims at obtaining the administrator tickets by listening to the changes of a specific logon account present only in systems that are managed with its use. It is called KRBTGT, and contains tickets that have a super user (administrator) privileges. Golden tickets never expire, and allow access to any service present in the system out-of-box.
Overpass-the-hash a.k.a. Pass-the-Key
When Mimikatz is able to reach the domain controller, things turn into a different manner. The hacktool, using a NTLM hash, gets a Kerberos ticket from the domain controller. Then, it uses this ticket, and a hacker is able to act just like after the successful pass-the-ticket attack. This kind of action is possible only if the current setup supposes the use of a backward-compatible way to generate the NTLM hash.
Another way for overpass-the-hash attack is spoofing the Kerberos ticket through giving the domain controller leaked AES keys. Once Mimikatz is running on a computer with proper AD permissions, it is capable of performing the DCSync command. The latter lists AES keys attributed to the current user.
Then, crooks may opt to command the hacktool to embed the leaked key to a Kerberos ticket. As the result, a ticket issued for another user will fit for the one which account is used for that hack, as Mimikatz issued a spoofed auth ticket signed with AES key.
How dangerous is Mimikatz?
It is not dangerous itself, despite having an extensive number of less-than-legit capabilities we listed above. Such programs are generally considered to be risky, as the vast majority of times their presence has malicious intent. Skilled users or computer support centres may use it to get the login credentials of lost accounts, thus seeing a detection of Mimikatz in your system during such operations is normal. Still, hacking Windows even for a benevolent purpose stands against the Windows EULA, so Microsoft is rightful to ban your licence if it acknowledges the case.
Malicious use, however, can do a lot of nasty things to the system and network. Being able to gain admin privileges after breaking into the system is often vital for a great number of cyberattacks. Generally, this task is accomplished with the use of exploit malware – complicated, hand-made and expensive. But why do hackers ever care when there is a free open-source tool that allows them to escalate privileges or simply dump the system login information of all users in the network. The fact this hacktool is getting updates each time Microsoft changes something in the targeted mechanisms makes Mimikatz as prolific as the most complicated malware samples.
The only thing that stops crooks from using it over and over again is its fame. Mimikatz is worldwide-known, the number of cyberattacks that have already happened with its participation is immense. Thus, even the most basic security solutions will have the measures specifically against this hacktool and its brethren. We may have seen the forks of this program, as it is open-source and may be edited by anyone. But both its methods and its brand are not very widespread nowadays.
How to protect yourself from Mimikatz?
We mentioned that Mimikatz typically appears as a part of a malware bundle during cyber attacks. Thus the ways to avoid this hacktool repeat the ones to prevent cyberattack. On the other hand, the hacktool exploits specific elements of the authentication system used in Windows and auxiliary Microsoft products. This part requires a separate piece of advice.
Mitigate human factor influence. Any complicated security measures are often rendered ineffective when an insider has no clue about cybersecurity rules. Show your employees how to distinguish between a genuine and fake email. Explain to them why it is risky to use random USB drives in the corporate networks. Instruct them to avoid sharing any details regarding used software and hardware solutions – to sharply decrease the efficiency of OSINT reconnaissance. In combination, it will not only decrease the chance of someone’s mistake, but will also make the hacker’s task more difficult.
Use network protection tool. A proper network security solution will not only protect you from attacks from outside the network, but also decrease the chances for a successful malware unfolding. Malicious software that provides initial access – backdoors, remote access trojans or malware droppers – often perform self-destruction after failing to connect to the command and control server. Attacks that involve malware delivery through vulnerable network protocols or hardware, can be mitigated as well. Network detection and response (NDR) systems are unified all-in-one solutions for network protection – consider checking them out.
Install advanced anti-malware software solution. Modern threats feature not only complexity in both structure and activity. Most of the time, they are designed specifically to avoid detection with most of the common rules. Thus, to protect against intruders you should apply something that goes beyond “classic” detection methods. EDR and derivative solutions will fit perfectly, as they generally feature heuristic detection and, what is more important, all-encompassing protection. It is created to track any activity within the perimeter, and give a solid, homogeneous response to a possible threat.
Specific reaction to Mimikatz is rarely needed, as this utility is perfectly known to anti-malware software developers. Hence, most often security tools already can detect the hacktool without any problem. That’s why it is better to implement counteraction measures against the ways it hacks the authentication methods – especially because the same attacks may be repeated using the hacktool other than Mimikatz.
Using Windows Defender Credential Guard. Microsoft always has had a peculiar view upon fixing their own bugs. Instead of reacting to Mr. Delpy’s notice, they released a separate security mechanism, which adds a layer of virtualisation between credential storage and the process that handles authentication. Establish it – and pass-the-ticket attacks will not be possible anymore.
Control access privileges. This measure will not cancel the possibility of attack, but will win you some time. Limiting the number of endpoints a single account can access will seriously slow the crooks down. Setting a fixed list of accessible elements, on the other hand, will reduce the potential of a single account even more. This or another way, hackers will have to look for another account to compromise - which may be not that easy.
Specific setup of Active Directory. Microsoft embedded a wide variety of settings that allow to change not only domain structure, but also authentication. Setting a shorter life for issued tickets, performing regular password resets and adjusting the accessibility of domain controller(s) will decrease the chance of successful pass-the-ticket attacks and its derivatives.




